H Homomorphic Encryption
What Is Homomorphic Encryption?
Homomorphic encryption is a form of encryption that allows to perform calculations on encrypted data without decrypting it first. The result of such computation is produced in encrypted form. When decrypted, the output is the same as if the calculations had been performed on the unencrypted data. [Wikipedia]
How Can It Be Useful?
Imagine a person who wants to perform some calculations but doesn't trust a calculator with their numbers:
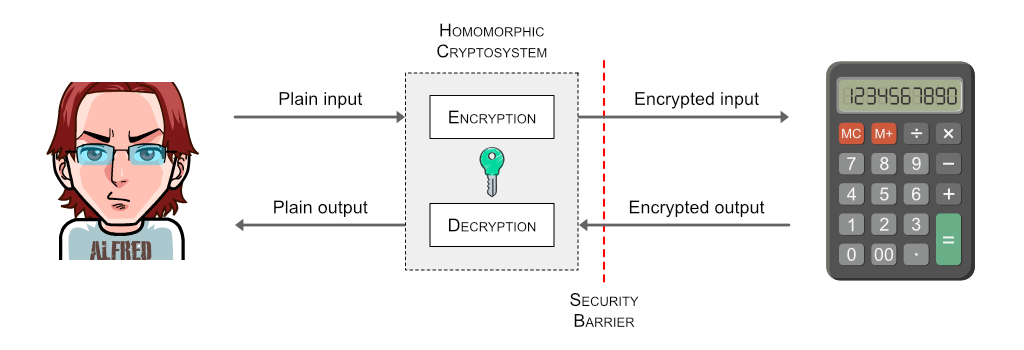
As it turns out, the whole scheme is pretty achievable with homomorphic encryption. Calculator performs the operations but never knows what exact data are being processed. The user is careful enough to encrypt all the numbers before entering them into calculator. And the only way to get a meaningful result back from calculator is to decrypt it with the same secret knowledge that was used for encryption.
The security barrier indicates that the user never shares its secret key with the calculator.
Homomorphic Encryption and Obfuscation
Eazfuscator.NET goes a long way to tie the homomorphic encryption and obfuscation together.
At first, it generalizes the calculator from a previous example as a universal Turing machine, so that not only the numbers but also programs (P) with their input (I) and output (O) data can be processed securely:
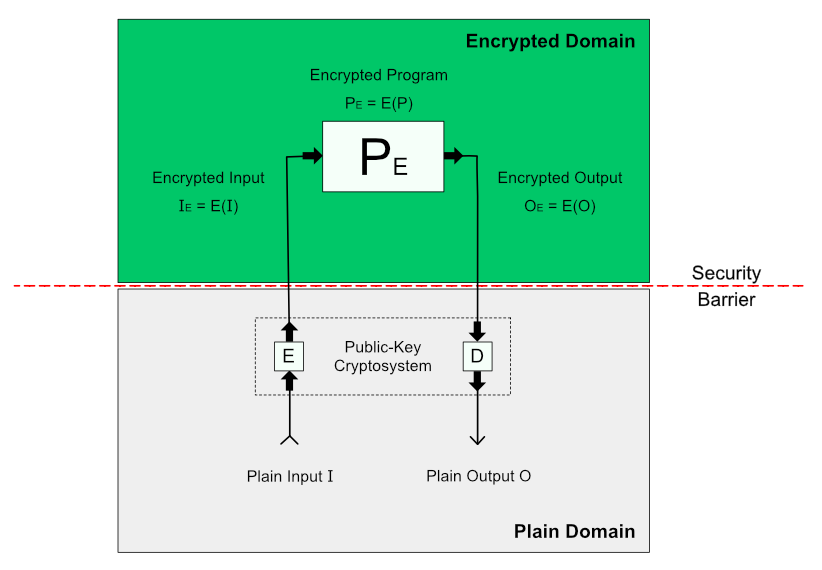
Then, Eazfuscator.NET deals with a problem of missing security barriers in runnable software by introducing Conditional Indistinguishability Obfuscation (CiO) model:
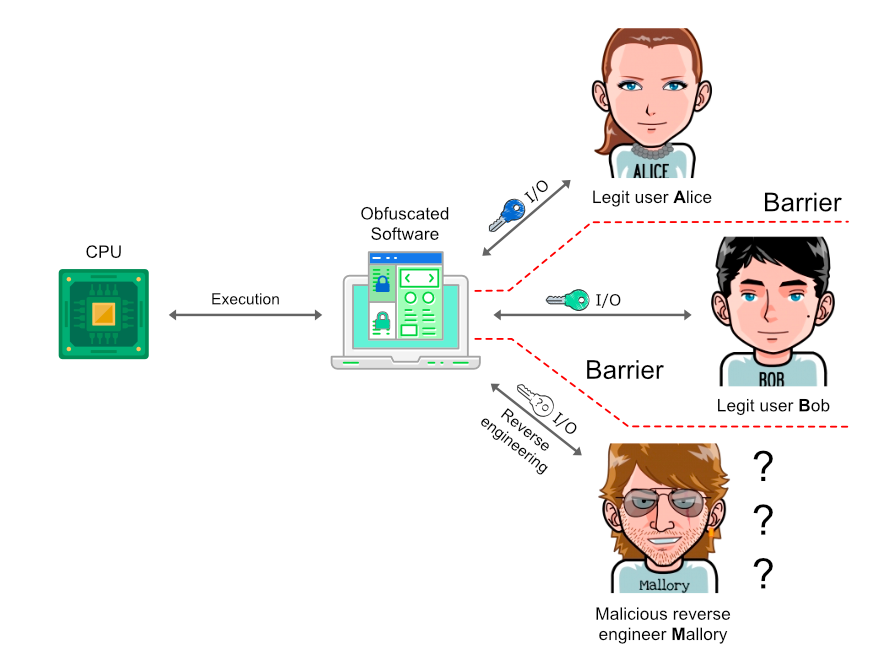
CiO model solves the code security dilemma and shapes the class of circuits Eazfuscator.NET can work on when it comes to homomorphic encryption.
In this way, homomorphic encryption allows Eazfuscator.NET to achieve the state of indistinguishable obfuscation for the specific parts of obfuscated programs.
If you are interested in even more details, you are welcome to read the corresponding publication.
Why Indistinguishable Obfuscation Is Important?
Indistinguishable obfuscation represents the highest level of intellectual property protection. It is synonymous to cryptographic obfuscation — both terms are used nearly interchangeably.
In practice, cryptographic obfuscation irreversibly transforms a program into encrypted form. Such an encrypted program can still run, but an attacker cannot decrypt it with the same level of guarantees as with traditional data cryptography unless he knows the secret key.
An important trick is that the secret key is never stored in the program. And the key is large enough to deter any practical attempts to brute-force it, while being compact enough to keep the performance in check.
How to Use Homomorphic Encryption in Eazfuscator.NET?
Whenever a method has a virtualization directive, its recognized code circuits get homomorphically encrypted:
using System;
using System.Reflection;
class YourClass
{
[Obfuscation(Feature = "virtualization", Exclude = false)]
void YourMethod()
{
...
}
}In this way, homomorphic encryption is applied to all virtualized methods automatically.
Homomorphic encryption is enabled with virtualization since the latter naturally transforms a program into data. And this is the exact representation required by homomorphic encryption in order to be useful in realm of obfuscation. They literally are a perfect match.
